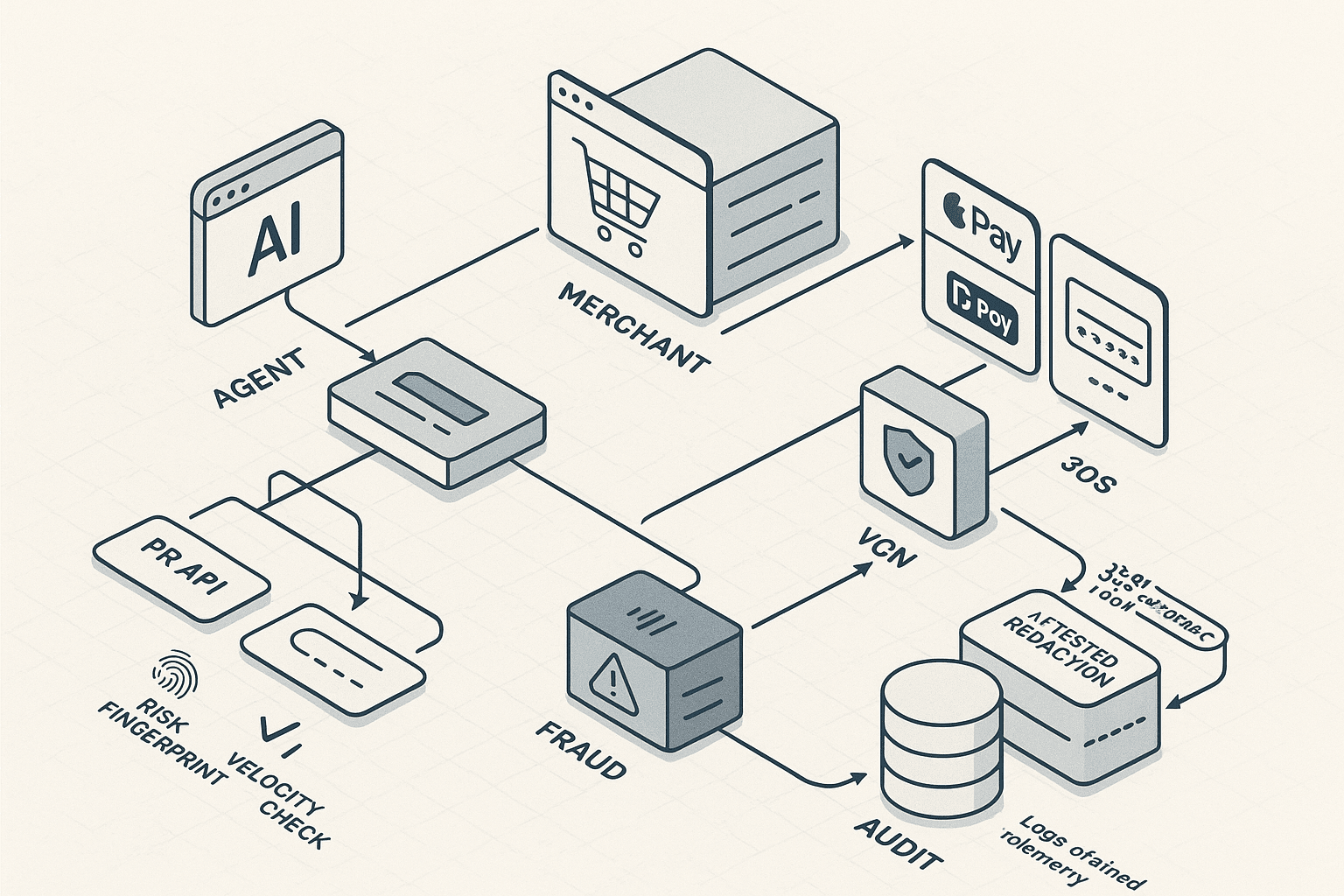
Executive summary
AI browser agents can already navigate, fill forms, and press “Buy.” Turning that into a production-grade, compliant checkout system is harder: you must narrow PCI DSS scope, survive SCA/3DS challenges, integrate Payment Request API and wallets when available, implement robust fraud controls, and ensure auditability and idempotency so you never double-charge. This guide presents an engineering blueprint to ship a PCI-safe checkout agent that operates across arbitrary merchant sites in a real browser, with opinionated patterns that minimize risk and operational drag.
Key outcomes you should target:
- PCI scope minimization: Use virtual cards (VCNs) and tokenization so your systems never store or transmit raw PAN/CVV. Keep sensitive data client-side and ephemeral.
- SCA readiness: Gracefully handle EMV 3DS2 flows, including frictionless, decoupled, and challenge modes; don’t try to “work around” SCA.
- Wallet-first: Prefer Payment Request API with Apple Pay/Google Pay where supported to avoid PAN exposure and reduce friction.
- Fraud controls: Add device- and user-level velocity, merchant allow-lists, per-transaction limits, and user presence checks.
- Attested redaction: Prove that logs/telemetry cannot leak PAN/CVV/PIN by design. Use hardware-backed keys and verifiable redaction.
- Idempotency and auditability: One intent → one charge. Provide defensible logs and replay-safe execution across retries.
Threat model and PCI scope
What you must assume:
- The agent operates a real browser via Playwright/Selenium/CDP. It may type into arbitrary HTML forms and iframes.
- Merchant pages are untrusted. They may load third-party scripts. They may block automation if they detect it.
- You cannot rely on direct PSP integration because merchants vary; your agent must adapt to each site’s checkout.
PCI scope goals:
- Keep your server out of PCI DSS scope as much as possible. The strictest control applies once your systems see PAN/CVV.
- Store and process payment credentials only on the user’s device, ideally inside a secure enclave or OS keychain. Prefer tokens over PAN.
- Never print or log PAN/CVV. Enforce redaction at the SDK boundary, not as an afterthought in application code.
Narrowing scope with tokenization and virtual cards
The safest path is to never handle primary account numbers (PAN) directly in your backend. Two complementary tools help:
- Virtual Card Numbers (VCNs):
- Issuer processors like Stripe Issuing, Lithic, and Marqeta can mint single-use or merchant-locked VCNs with limits (amount, MCC, velocity), expiration, and fine-grained controls.
- VCNs give you “hardware” idempotency: set a single-use, single-merchant, single-amount cap and let the issuer enforce exactly-once by declining duplicates.
- If the merchant is unknown (arbitrary merchant checkout), use dynamic VCNs with narrow controls:
- Merchant category code (MCC) allowlist or target MCC range.
- Spend cap equal to expected total + slippage.
- Timebox (e.g., 30 minutes).
- Optional merchant descriptor lock when predictable.
- Network tokenization and wallets:
- Apple Pay and Google Pay replace PAN with DPAN/tokens and cryptograms. Payment Request API can route to these methods. The PAN never enters the page or your code.
- Where the merchant supports Payment Request API methods like https://google.com/pay or https://apple.com/apple-pay, prefer those flows.
Recommended hierarchy for credential usage:
- Tier 1: Wallet via Payment Request API (Apple Pay/Google Pay) → minimal PCI scope, issuer cryptograms, risk scoring upstream.
- Tier 2: Virtual card with strict controls inserted into form fields when wallet is unavailable.
- Tier 3: Avoid raw PAN entry entirely unless you control the checkout stack (rare for an agent spanning many merchants).
Architecture overview
- Agent runtime: Browser automation worker (e.g., Playwright) running on the user’s device or a trusted compute node. Must support input simulation, iframe navigation, and intercepting modals.
- Policy brain: Decides which payment method to attempt (wallet vs VCN vs abandon), thresholds, and fallbacks.
- Payment credential service: Issuer API for VCN creation, lifecycle management, and authorization webhooks.
- SCA/3DS handler: Detects and satisfies challenges using in-browser prompts, decoupled authentication, or user push to issuer app.
- Fraud/risk service: Velocity, device fingerprint, merchant allow-list, geofencing, behavioral checks, and user presence.
- Observability and attested redaction: Telemetry pipeline that never exfiltrates PAN/CVV and produces verifiable redaction proofs.
- Audit and idempotency store: Hash-chained logs, idempotency keys, purchase intent ledger, and reconciliation workers.
Handling SCA and 3DS2 without breaking UX
EMV 3-D Secure (3DS2) under PSD2 SCA requires strong customer authentication for most card-not-present transactions in EEA/UK. Outside those regions, 3DS2 is still common for risk control. Your agent must be SCA-compatible:
Know the 3DS2 modes:
- Frictionless: Issuer decides no challenge. The merchant sends device data; transaction proceeds silently.
- Challenge: The issuer presents a challenge (OTP, app push, knowledge-based). Appears in an iframe (challenge window) or in a separate flow.
- Decoupled (OOB): Issuer authenticates via its app independently of the browser (push, FaceID). Merchant poll completes later.
Agent strategies:
- Don’t bypass. Your agent should surface the challenge to the user (e.g., native push to the issuer app or embedded OTP prompt). Absent user presence, abandon gracefully.
- Timeouts and retries: Many 3DS challenges have 5–10 minute windows. Implement backoff and a single retry if the user re-approves.
- UX: Provide crisp prompts: “Approve purchase in your banking app” with a countdown.
- Accessibility: If challenge is an iframe, focus it and mirror the UI state to the user in your own UI (without scraping PII).
Detecting 3DS in the wild:
- Look for iframes with known ACS/3DS domains or window titles like “Secure Checkout / Verification.”
- Observe network calls to 3DS servers (e.g., challenge-init endpoints). Maintain a signature catalog for common gateways (Adyen, Stripe, Braintree, Worldpay, Checkout.com, etc.).
- Heuristic fallback: if the final payment button returns to the same page with an iframe overlay, assume challenge.
A minimal Playwright pattern for challenge handling
ts// Typescript/Node (Playwright) import { chromium } from 'playwright'; async function handle3DS(page) { // Wait for a 3DS challenge iframe (heuristics: role, title, vendor domains) const challengeFrame = await page.frame( f => /3ds|challenge|secure|acs/i.test(f.name() || '') || /acs|secure|3ds/i.test(f.url()) ); if (!challengeFrame) return false; // Might be frictionless // Example: wait for OTP input if present const otpSelector = 'input[type="tel"], input[name*="otp" i], input[id*="otp" i]'; const input = await challengeFrame.waitForSelector(otpSelector, { timeout: 5000 }).catch(() => null); if (input) { const otp = await requestOtpFromUser(); // Trigger native prompt / push; do not log await input.fill(otp); await challengeFrame.click('button:has-text("Submit"), button[type=submit]'); } else { // Decoupled or app-push; notify user and wait notifyUserToApproveInIssuerApp(); await challengeFrame.waitForSelector('text=/approved|successful|complete/i', { timeout: 180000 }); } return true; }
Payment Request API first, when possible
Payment Request API (PR API) reduces friction and removes PAN from page scripts by invoking browser-native payment handlers like Apple Pay or Google Pay. Caveats:
- The legacy "basic-card" method is deprecated. Rely on method-specific handlers: https://google.com/pay, https://apple.com/apple-pay.
- A user gesture is required to trigger PR API. Your agent should perform a real click.
- Merchant must register accepted methods; your agent cannot force PR API if the site does not support it.
Detect PR API on a page:
js// Evaluate in page context async function canUsePaymentRequest(supportedMethods) { if (!('PaymentRequest' in window)) return false; try { const details = { total: { label: 'Total', amount: { currency: 'USD', value: '19.99' } }, }; const request = new PaymentRequest(supportedMethods, details); return await request.canMakePayment(); } catch (e) { return false; } }
Invoke PR API (example skeleton; method-specific data omitted):
js// Must be called from a user gesture (click handler) async function payWithGooglePay() { const supportedInstruments = [{ supportedMethods: 'https://google.com/pay', data: {/* merchantId, allowedAuthMethods, tokenizationSpecification, etc. */} }]; const details = { total: { label: 'Total', amount: { currency: 'USD', value: '19.99' } }, }; const request = new PaymentRequest(supportedInstruments, details); const response = await request.show(); // The merchant site normally processes response.details; your agent shouldn’t access card payloads await response.complete('success'); }
In practice, your agent should:
- Probe for PR API acceptance by reading the page’s registered payment methods (if exposed) or by DOM heuristics (Apple/Google Pay buttons).
- Prefer clicking the site’s own wallet buttons; those often integrate PR API or JS SDKs with fewer surprises.
- If PR API is unavailable, fall back to VCN form fill.
Virtual card provisioning and controls
When PR API is unavailable or fails, generate a VCN with strict controls before form fill. Example with Stripe Issuing (pseudocode; adapt to your provider):
python# Python import stripe stripe.api_key = os.environ['STRIPE_KEY'] # 1) Create a new single-use virtual card with spend controls issuing_card = stripe.issuing.Card.create( cardholder='ich_123', currency='usd', type='virtual', spending_controls={ 'spending_limits': [{ 'amount': 2150, # $21.50 in cents 'interval': 'single_purchase' }], 'allowed_categories': ['electronics_stores', 'computer_software_stores'], 'allowed_merchant_countries': ['US'], }, metadata={ 'intent_id': 'buy-merchant-xyz-abc123' } ) # 2) Retrieve PAN details only inside a secure local runtime (never send to backend logs) number = issuing_card.number cvc = issuing_card.cvc exp_month = issuing_card.exp_month exp_year = issuing_card.exp_year
Enhancements:
- Merchant lock: Some issuers support pre-authorizing a merchant descriptor or merchant ID. If the site is predictable, set it. Otherwise, restrict MCCs.
- One-and-done: If the purchase fails, dispose of the VCN and create a new one for the next attempt to preserve idempotency.
- Webhooks: Consume authorization webhooks to reconcile attempts and show real-time success/decline reasons.
Secure form fill without leaks
- Autofill strictly the minimum: PAN, expiry, CVC, name, and billing ZIP. Do not store form field values outside the page context.
- Disable screenshots and page recordings around payment entry unless fully redacted. Consider drawing a black overlay rectangle around the form before any capture.
- Instrument your telemetry SDK so that any DOM extraction from payment fields is denied at source, not just redacted downstream.
Fraud controls suited for AI agents
Even if you’re transacting on behalf of the user with their card or a VCN, you still need guardrails.
- Merchant allow-list: Maintain a list of known, vetted merchants. For long-tail sites, require explicit user approval for first-time purchases.
- Spend policy: Per user/device daily caps, per-merchant caps, and per-transaction maximums.
- Device fingerprint: Bind purchase attempts to a stable device identifier (privacy-preserving) using browser characteristics and OS attestation where available. Avoid invasive tracking; you only need enough stability to enforce velocity rules.
- User presence: Require a quick confirmation (passkey/WebAuthn/FaceID/TouchID) before releasing a VCN or clicking Buy on a new merchant.
- Geofencing & IP hygiene: Unexpected geolocation or network anomalies should raise friction (e.g., require extra user confirmation).
- Behavioral checks: Sudden cart price jumps, shipping address anomalies, or unusual SKU patterns trigger review.
SCA exemptions and when to apply them
- Low-value (< €30) and Transaction Risk Analysis (TRA) exemptions can reduce challenges, but only the merchant/acquirer can claim them. Your agent cannot force an exemption on arbitrary sites.
- MIT/CIT distinctions matter when you own the merchant flow. As an external agent you’re in cardholder-initiated territory.
Attested redaction: verifiable privacy for logs and telemetry
A critical failure mode: leaking PAN/CVV in logs or traces. Don’t rely on developer discipline; build a pipeline that makes leaks cryptographically unlikely and auditable.
Pattern:
- Client-side classification: Tag all telemetry fields with data classes (pci.pan, pci.cvv, pii.email, etc.) at the SDK edge.
- In-enclave redaction: Run an OpenTelemetry processor inside a secure enclave (e.g., Apple Secure Enclave/Keychain, Android StrongBox, or SGX/SEV on servers). Redact and HMAC sensitive fields with a hardware-protected key. Only hashed tokens leave the enclave.
- Attestation: Generate a hardware attestation of the redaction binary (measurement), include it in a signed startup record, and chain subsequent log batches to that record.
- WORM storage and transparency: Write audit logs to append-only storage, optionally mirrored to a transparency ledger (e.g., Sigstore/Rekor) with hash chaining.
Example: OpenTelemetry redaction processor (pseudocode)
go// Go pseudo-processor that runs in a TEE; never emits raw PAN/CVV func Redact(record LogRecord) LogRecord { for k, v := range record.Attributes { if IsPCIField(k) { record.Attributes[k] = HMAC(enclaveKey, Truncate(v, 6)) // first 6 for troubleshooting record.Attributes[k+".redacted"] = true } } record.Attributes["redaction.attestation"] = enclaveAttestationQuote() return record }
Secure UI prompts: when requesting OTP from the user, route through a system native prompt that is isolated from page scripts. Never echo OTP into logs.
Idempotency: one intent, one charge
For an agent spanning many merchants, you cannot rely on a unified payment API to deduplicate charges. Combine protocol and product levers:
- Intent ledger: Every purchase attempt has a deterministic idempotency key: hash(user_id, merchant_domain, sku_or_cart_fingerprint, total_amount, currency, shipping_address, timestamp_bucket). Store state transitions: planned → executing → authorized → captured → failed → abandoned.
- VCN single-use limit: Make the issuer enforce exactly-once by rejecting duplicate authorizations.
- Merchant confirmation detection: Use DOM signatures for order confirmation pages and email receipt ingestion to mark success. Do not rely solely on “button click success.”
- Retry rules: Safe retry window with invariants:
- Never reuse a VCN after an unknown error.
- If merchant order already exists (detectable by confirmation number on account/orders page or email), abort payment and mark as succeeded.
Sample idempotent orchestration with an outbox
ts// Pseudocode async function purchase(intent) { const key = computeIdempotencyKey(intent); return await db.tx(async (tx) => { const row = await tx.getOrCreateIntent(key, intent); if (row.state === 'succeeded') return row; if (row.state === 'executing') throw new Error('In-flight'); await tx.updateState(key, 'executing'); // Provision single-use VCN with amount cap const vcn = await provisionVCN(intent.total, intent.policy); try { const success = await runCheckoutFlow(intent, vcn); if (success) { await tx.updateState(key, 'succeeded'); await outbox.enqueue({ type: 'reconcile', key }); } else { await tx.updateState(key, 'failed'); } } catch (e) { await tx.updateState(key, 'failed'); throw e; } finally { await revokeVCN(vcn); } return await tx.getIntent(key); }); }
Auditable purchases: build a defensible trail
- Structured events: purchase.intent, purchase.attempt, sca.challenge, authorization.approved, capture.succeeded, reconciliation.completed.
- Correlation IDs: Propagate a trace_id across browser automation, VCN provisioning, and issuer webhooks.
- Hash chaining: Each audit record includes prev_hash; anchor daily summaries in an external immutable store.
- Data minimization: Store only what you need for dispute resolution. Tokenize PII and use keyed pseudonyms.
Interfacing with anti-bot systems (ethically)
- Respect merchant terms. Do not circumvent anti-bot measures. Your agent should imitate a real user session with real user presence and gestures.
- Avoid headless-only fingerprints. Use headed browsers when possible and simulate natural input timing.
- Be ready to fall back: If the site blocks automation, surface a prompt to the user to complete manually.
Checkout flow blueprint
- Pre-flight
- Validate policy: merchant allow-list, spend cap, geofencing, user presence check (WebAuthn).
- Compute idempotency key and check ledger.
- Prepare VCN policy but don’t reveal PAN yet.
- Wallet attempt
- Detect and prefer Apple Pay/Google Pay buttons or PR API.
- Trigger via a real click. If SCA challenge arises, handle via system prompts. On success, stop.
- VCN fallback
- Provision a single-use VCN with amount cap.
- Fill form fields securely; bind shipping/billing addresses.
- Submit payment; handle 3DS challenge.
- On success, immediately revoke or zero out remaining VCN limits.
- Confirmation and reconciliation
- Wait for order confirmation page signature.
- Poll issuer authorization webhooks for a matching approval.
- Optionally monitor email inbox for receipt (with user consent). Mark intent as succeeded when two of three signals match.
- Post-purchase
- Emit signed audit records with attestation.
- Revoke VCN and delete sensitive data from memory.
- Update velocity counters.
Handling real-world 3DS gotchas
- Nested iframes: Many ACSES run inside double iframes. Enumerate frame tree, prefer vendor-domain matches.
- Keyboard traps: Some challenge forms trap focus; simulate tab/enter carefully.
- OTP delivery delays: Provide a resend mechanism by clicking the vendor-provided link, not resubmitting the whole form.
- Decoupled approvals: Poll with exponential backoff; set a clear timeout and revert.
Security posture for the agent runtime
- Secret isolation: Use OS keychains and hardware-backed keys. Never store PAN or OTP at rest.
- Memory hygiene: Zeroize buffers after use where language permits. Avoid long-lived strings with PAN.
- Screenshot governance: Redact or disable around payment forms by default.
- Supply chain: Pin your automation stack versions; enable sandboxing and seccomp where available.
- Permissions: Minimal network egress; restrict clipboard and file system access.
Testing strategy
- Synthetic merchants: Stand up a testbed with known 3DS2 flows (frictionless, OTP, app push). Gate agent releases on these cases.
- Issuer sandboxes: Use your VCN provider’s sandbox to simulate declines, insufficient funds, merchant mismatch, and velocity caps.
- Real-device matrix: Test on macOS/Windows/Linux and iOS/Android browsers to validate PR API and wallet behavior.
- Chaos: Inject network jitters and timeouts during challenge windows.
Monitoring and SLOs
- SLOs to track: Wallet success rate, VCN success rate, 3DS challenge rate, challenge success rate, duplicate-prevented rate, mean time to purchase, abandonment.
- Risk KPIs: Fraud rate, false-positive blocks, velocity rule triggers, dispute ratio.
- Privacy metrics: Redaction coverage (% of sensitive fields HMAC’d), attestation verification rate.
Example: detecting wallet buttons before form fill
tsasync function findWalletPreference(page) { const applePayBtn = await page.$('button[aria-label*="Apple Pay" i], apple-pay-button'); const gpayBtn = await page.$('button[aria-label*="Google Pay" i], div[role="button"][aria-label*="GPay" i]'); if (applePayBtn) return { type: 'apple' }; if (gpayBtn) return { type: 'google' }; return { type: 'none' }; }
Example: user presence via WebAuthn before releasing VCN
ts// Browser context: request a quick assertion to confirm the user is present async function confirmUserPresence() { const cred = await navigator.credentials.get({ publicKey: { challenge: crypto.getRandomValues(new Uint8Array(32)), allowCredentials: [], timeout: 30000, userVerification: 'preferred' } }); return !!cred; // Do not log cred details }
Compliance notes
- PCI DSS scope: If your backend never processes PAN/CVV and only handles tokens and issuer webhooks, you reduce scope substantially. The client agent remains in scope; treat it as a SAQ A-EP-like environment on the device with strict controls.
- PSD2 SCA: Do not design to avoid SCA. Design to comply: surface challenges, support decoupled flows, and respect timeouts.
- Data retention: Keep the minimum needed for dispute resolution. Use tokenized references and WORM storage for audit integrity.
Decision matrix: when to abandon
- Merchant blocks automation or injects anti-bot captchas you cannot ethically satisfy.
- Wallet absent, form highly obfuscated, and 3DS likely to fail due to strict anti-automation.
- Price or cart changes mid-flow beyond policy thresholds.
- User does not respond to SCA within permitted window.
Operational playbook
- Rollout: Start with a curated merchant list and wallet-first flows. Gradually expand to form-fill with VCNs.
- Incident response: If duplicate charges suspected, freeze retries, revoke VCNs, and contact issuer support with authorization IDs. Use your audit log to reconcile quickly.
- Tuning: Adjust velocity thresholds and per-merchant caps based on dispute feedback and success rates.
FAQ
- Is Payment Request API widely supported? It’s supported in modern browsers, but actual merchant adoption is uneven. Many use provider SDKs (GPay/Apple Pay) instead of bare PR API. Your agent should click the merchant’s wallet buttons when present.
- Can the agent pass SCA without the user? Not ethically or reliably. Use decoupled approvals to shift authentication to the issuer app, or prompt the user for OTP.
- Does a VCN guarantee no fraud? No, but it narrows the blast radius with spend caps and merchant controls. Combine it with device/user checks.
- Do I need PCI certification? If your backend never stores/transmits PAN/CVV and you strictly confine sensitive handling to the user’s device into wallets/VCNs, your server scope can be very limited. Still, seek a QSA’s advice for your specific architecture.
References and further reading
- EMV 3-D Secure 2.x specifications (EMVCo)
- PSD2 and EBA RTS on SCA and secure communication
- W3C Payment Request API and Payment Handler API
- Apple Pay on the Web and Google Pay API documentation
- PCI DSS v4.0 standard and SAQ guidance
- Stripe Issuing, Lithic, Marqeta documentation on virtual cards and spend controls
- OpenTelemetry specification and processor development
- Sigstore/Rekor transparency logs and WORM storage patterns
A concise checklist
- Wallet-first: Try Apple Pay/Google Pay via PR API or provider buttons.
- If wallet unavailable: Provision single-use VCN with tight caps and MCC filters.
- Handle SCA: Surface challenge; support OTP and decoupled approvals.
- Fraud controls: Allow-list merchants, enforce velocity and device fingerprinting, require user presence.
- Attested redaction: Hardware-backed redaction with OTel; no PAN/CVV leaves the enclave.
- Idempotency: Intent ledger, VCN single-use, safe retries, and merchant confirmation detection.
- Auditability: Hash-chained logs, correlation IDs, and minimal yet sufficient retention.
Conclusion
A production checkout agent must be more than a macro that presses Buy. By leaning on wallets and tokenization, you minimize PCI DSS exposure. By embracing 3DS/SCA instead of fighting it, you keep approval rates high and compliant. By building fraud controls, attested redaction, and strong idempotency and audit guarantees, you create a system that stakeholders—security, compliance, and users—can trust. The blueprint above is intentionally opinionated: wallet-first, VCN-backed, user-present, and verifiably private. With these constraints, your AI browser agent can safely and reliably transact across the web.